Zero Trust Security
Based on the principle of “never trust, always verify,” First Datacorp’s Zero Trust Security solutions helps secure corporate resources by eliminating unknown and unmanaged devices and limiting lateral movement. Implementing a true Zero Trust model requires that all components—user identity, device, network, and applications—be validated and proven trustworthy. Zero Trust verifies identity and device health prior to granting access to corporate resources. When access is granted, applying the principle of least privilege limits user access to only those resources that are explicitly authorized for each user, thus reducing the risk of lateral movement within the environment. In an ideal Zero Trust environment, the following four elements are necessary:
- Strong identity authentication everywhere (user verification via authentication)
- Devices are enrolled in device management and their health is validated
- Least-privilege user rights (access is limited to only what is needed)
- The health of services is verified (future goal)
Three Pillars of Zero Trust Security
Zero Trust Security solution suite is a breath of best in class solutions from Microsoft, BMC Software, Cisco and F5, complementing each other to provide organizations with the following business benefit:
- Decreases risk by discovering assets and improving visibility
- Provides business and client data protection
- Gain greater control in your cloud environment
- Achieve lower breach potential
- Aid compliance audit initiatives
- Increase business speed and agility
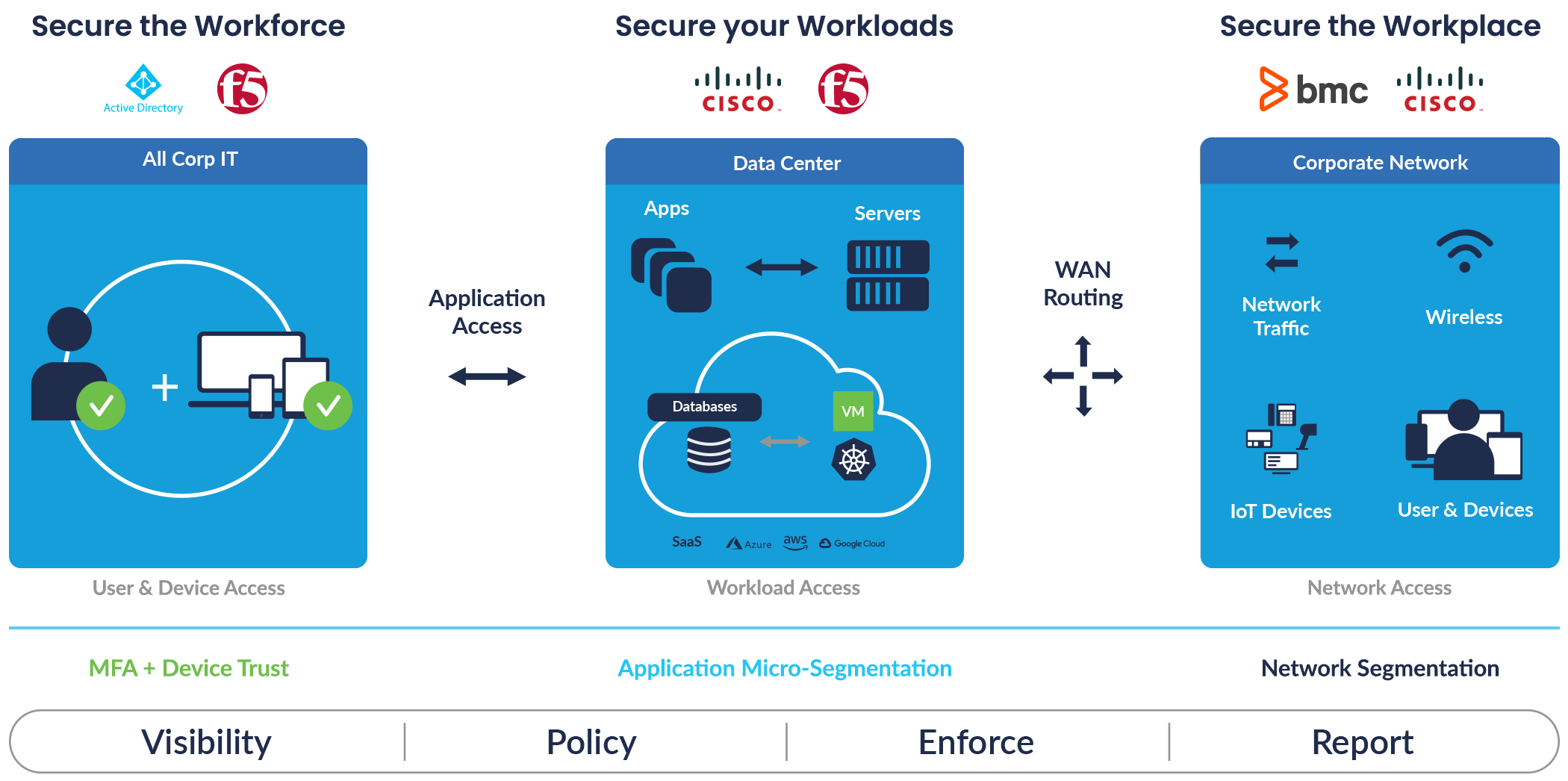
Secure the Workforce
Zero Trust Secure the Workforce solution is leveraging on Azure Active Directory and F5 Security on making sure users and devices can be trusted as they access systems, regardless of location. It establishes trust in users and devices through authentication and continuous monitoring of each access attempt, with custom security policies that protect every application. It supports the following:
- Authentication: Manage Azure Active Directory self-service password reset, Multi-Factor Authentication, custom banned password list, and smart lockout.
- Busines to Business: Manage your guest users and external partners, while maintaining control over your own corporate data.
- Device Management: Manage how your cloud or on-premises devices access your corporate data.
- Identity Governance: Manage your organization's identity through employee, business partner, vendor, service, and app access controls.
- Identity Protection: Detect potential vulnerabilities affecting your organization's identities, configure policies to respond to suspicious actions, and then take appropriate action to resolve them.
- Report and Monitoring: Gain insights into the security and usage patterns in your environment.
Secure your Workloads
Zero Trust Secure the Workload solution focuses in preventing unauthorized access within application environments irrespective of where they are hosted. It leverages on Cisco and F5 security technologies to secure connections for all APIs, microservices, and containers that access your applications, whether in the cloud, data center, or other virtualized environment. It secures your app stack, and uses micro-segmentation to help contain threats and protect against lateral movement. It supports the following:
- Visibility into applications: Have control over every connection from users and devices to both your applications and your network, across a multicloud environment.
- Application segmentation: Minimize lateral movement for on-premises and multi-cloud environments.
- Monitor application performance: Identify root causes of threats with deep diagnostic capabilities.
- Enforce policies and controls: Enforce application-specific user and device access policies to meet your organization's security requirements for access. Flag anomalies using behavioral analysis to reduce your attack surface.
- Gain clarity into application architecture: Visualize every component and dependency, across any environment, with flow maps.
- Remediate threats quickly: Contain threats by quarantining any servers with anomalous processing behavior.
Secure the Workplace
Zero Trust Secure the Workplace solutions focuses on secure access for any and all devices (including Internet of Things (IoT)) that connect to enterprise networks, such as user endpoints, physical and virtual servers, printers, cameras, and more. Providing comprehensive, automated and secure device management that enables users to securely connect to your network from any device, anywhere while restricting access from non-compliant devices. It leverages on Cisco and BMC Software technologies to save time in securing endpoints from threats and vulnerabilities while reducing risk by automating policy compliance.
WITH FDC
First Datacorp is committed to protecting and respecting your privacy. We will only use your personal information to administer your account and to provide the solutions, products and services you have requested from us. By clicking 'submit' above, you consent to allow First Datacorp to store and process the personal information submitted above to provide you the content requested.